So you have decided to do some password auditing on YOUR domain.
It goes without saying that no one but yourself is liable if you use any of this information for nefarious of ‘black hat’ purposes.
This information is for System Admins and the like who are interested in taking a peek into their users password habits, and for developing password policies.
Here’s what you need to know:
-Extract the NTDS File from your Domain controller, via whatever method you want, (VSS, or backups).
-Export the SYSTEM registry Key
reg save HKLM\SYSTEM C:\<YOUR DIRECTORY>\filename
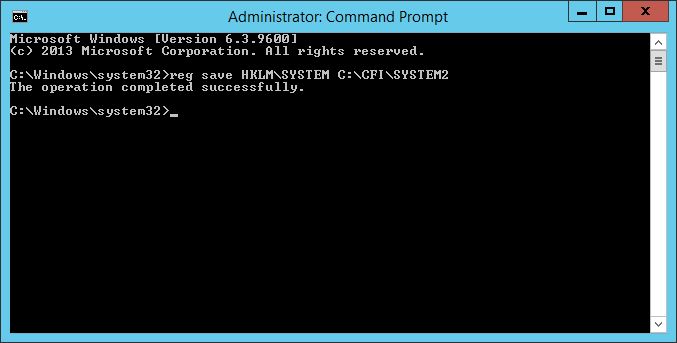
Happy days, you have 2 files you need.
Start PowerShell as an Administrator, and change the Security policy to allow other scripts to run:
Set-ExecutionPolicy -ExecutionPolicy Unrestricted
Looking over at DSInternals go ahead and download their package. If its not there, click here.
Download and install the module.
This module will open up the NTDS file and export the Hash’s that we will use later.
Install-Module DSInternals
Then Setup the $KEY variable with the location of you SYSTEM archive (that contains the decryption key).
$key = Get-BootKey -SystemHivePath 'C:\Password cracking\SYSTEM'
Now its time to dump the hash’s!
Get-ADDBAccount -All -DBPath 'C:\Password cracking\NTDS\ntds.dit' -BootKey $key | Format-Custom -View HashcatLM | Out-File cathashesLM.txt -Encoding ASCII
This command will spit out a file called cathashesLM.txt in your current working directory.
You can also spit the has’s out in the following ways: HashcatNT, JohnNT, JohnLM and Ophcrack
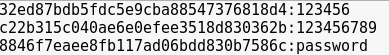
You should now have a file containing all the usernames and hash’d passwords that looks a little like this:
User1:2e269d776d5eee68e487522ae7a38671
User2:32ed87bdb5fdc5e9cba88547376818d4
User3:8846f7eaee8fb117ad06bdd830b7586c
(Go on, decrypt those ones!)
Go out and have a search online for a good password list like the rockyou list (containing about 14mil. passwords).
The bigger the better, i’m sure you can find some better ones out there, but the rockyou list is pretty darn good!
Now you should have 2 files,
-Usename and Password hash file
-Wordlist containing probable passwords
Fire up Kali and open Terminal and use the following command:
hashcat -m 1000 -a 0 --username <PATH TO YOUR HASH FILE> <PATH TO PASSWORD LIST> -0 matched_passwords
![]()
There will now be a file called matched_passwords in the working directory of terminal.
The file contains the password hash’s of passwords it found using the supplied password list.
It went and converted the passwords’s to hash’s and spat out ones that matched your hash file.
Now the fun part begins, copy the matched_Passwords file over to your Windows (or whatever computer has a spreadsheet software) computer again, along with the hash file and fire up our friend Excel.
Using VLOOKUP, you can compare the 2 files and see where the hash’s match!
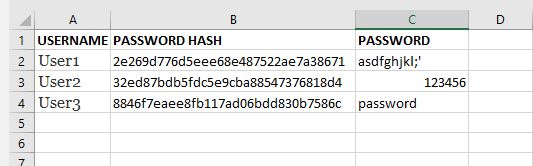
To do:
-Go and get these probable word list files: https://github.com/berzerk0/Probable-Wordlists and run again!
-Find a GPO to add most common passwords to be disallowed.
